SS
Size: a a a
2020 October 30
Проблема может быть только в размере базы РКН))
IA
🚨🚨🚨 INCREASED RANSOMWARE ACTIVITY
Over the last 48 hours the Check Point Incident Response Team (CPIRT) has seen a marked increase in Trickbot/Ryuk ransomware cases globally. This increase in activity has been supported by FBI, US-CERT and HHS notifications. We have seen an increase in targeting toward the health care industry, but it is important to note that we are also seeing increases in targeting toward additional verticals.
It is vital that customers take proactive measures immediately to protect their environments from aggressive ransomware activity.
Please consider the following controls:
1. Additional email security controls to protect against email threats such as Phishing, malspam, etc
2. Advanced Endpoint Controls such as SBA with Threat Hunting capabilities
3. File based protections – Threat Emulation/Threat Extraction
4. A full review of Active Directly to limit exposure to lateral movement techniques
5. IPS Controls to protect against DNS Tunneling
6. Ensure additional controls around RDP
As always the Check Point Incident Response, CP<R> and Threat Intelligence Operations Teams are vigilantly monitoring the situation and ensuring that Check Point products and services are covering all threat vectors.
In the event your customer/partner needs assistance please contact emergency-response@checkpoint.com or call at any of the numbers listed here - https://www.checkpoint.com/support-services/threatcloud-incident-response/
Over the last 48 hours the Check Point Incident Response Team (CPIRT) has seen a marked increase in Trickbot/Ryuk ransomware cases globally. This increase in activity has been supported by FBI, US-CERT and HHS notifications. We have seen an increase in targeting toward the health care industry, but it is important to note that we are also seeing increases in targeting toward additional verticals.
It is vital that customers take proactive measures immediately to protect their environments from aggressive ransomware activity.
Please consider the following controls:
1. Additional email security controls to protect against email threats such as Phishing, malspam, etc
2. Advanced Endpoint Controls such as SBA with Threat Hunting capabilities
3. File based protections – Threat Emulation/Threat Extraction
4. A full review of Active Directly to limit exposure to lateral movement techniques
5. IPS Controls to protect against DNS Tunneling
6. Ensure additional controls around RDP
As always the Check Point Incident Response, CP<R> and Threat Intelligence Operations Teams are vigilantly monitoring the situation and ensuring that Check Point products and services are covering all threat vectors.
In the event your customer/partner needs assistance please contact emergency-response@checkpoint.com or call at any of the numbers listed here - https://www.checkpoint.com/support-services/threatcloud-incident-response/
2020 November 01
МП
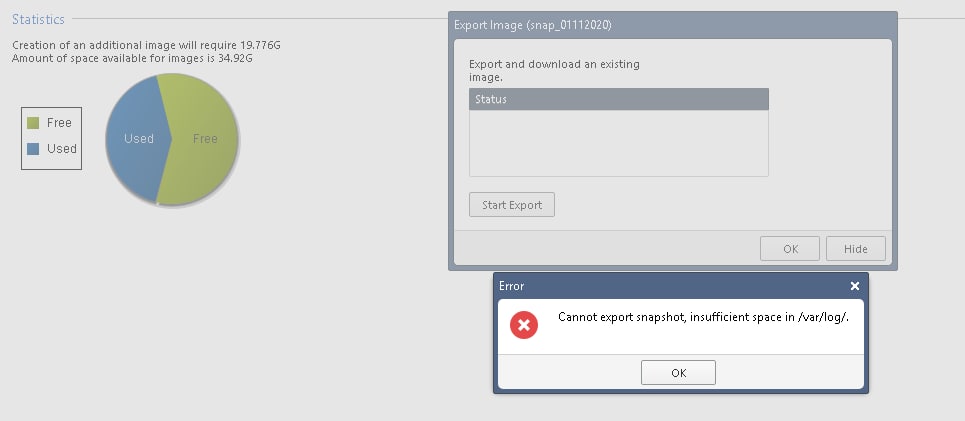
Коллеги, добрый день.
Нужен Ваш профессиональный совет.
Как выдернуть снапшот?
Нужен Ваш профессиональный совет.
Как выдернуть снапшот?
МП
Логи вычистил. Что ещё можно почистить?
СБ
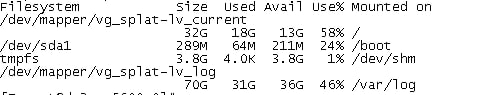
Добрый день. df -h что говорит?
МП
Добрый день. df -h что говорит?
СБ
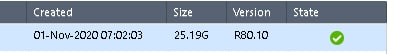
Снапшот больше 36G?
МП
Снапшот больше 36G?
СБ
IA
Должно быть свободно 2х snapshot size
IA
Эт чо за платформа?
IA
Да я понимаю, железка
МП
Checkpoint 5600
IA
Странный лэйаут диска
IA
А покажите pvs; vgs; lvs
МП
А покажите pvs; vgs; lvs
Илья, можно подробнее
IA
Вот команду в эксперт скопируйте прям как написано
IA
И скрин покажите
IA
Это листер разделов lvm, если что :)