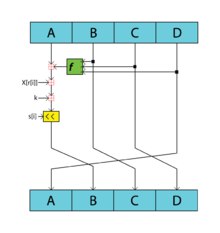
a
Size: a a a
2020 May 15
Is there any other algo that has 16-byte HMAC output?
a
Вопрос сфорвардил
MO
I understand this completely, with a bit of effort
I just think that is quite interesting experiment in linguistics
a
пойду работать
MO
ofk all speakers of slavic languages need some effort to understand it
J
I have a serious question now that you mentioned crypto. There's a CTF challenge asking me to provide a file and HMAC, and says the HMAC should be 16-byte (32 hex characters). I tried MD4 and MD5 HMAC, but it says "HMAC mismatch".
message authentication code
PK
yeah , padding is the problem.
what kind of problem, man?
PK
what do you need to do?
AA
Вопрос сфорвардил
О, спасибо
a
I have a serious question now that you mentioned crypto. There's a CTF challenge asking me to provide a file and HMAC, and says the HMAC should be 16-byte (32 hex characters). I tried MD4 and MD5 HMAC, but it says "HMAC mismatch".
PK
Padding is used to fill up plaintext to the blocklength of the cipher. This is not needed for counter mode, since it has no blocks and can encrypt any length.
There are different styles of padding, some are optimized to recognize changes or the actual length of the data. In case of the SSH sheme where a extra field specified the length no special pattern is needed, so random content provides the least information for attackers.
In SSH you can add padding longer than to the end of the block (I.e. To the next block or even more). This helps to make it harder for attackers to guess the actual plaintext length.
Especially for command/response sessions a lot can be learned if the cipher leaks the length. This is called traffic analysis and random padding length somewhat helps against it.
There are different styles of padding, some are optimized to recognize changes or the actual length of the data. In case of the SSH sheme where a extra field specified the length no special pattern is needed, so random content provides the least information for attackers.
In SSH you can add padding longer than to the end of the block (I.e. To the next block or even more). This helps to make it harder for attackers to guess the actual plaintext length.
Especially for command/response sessions a lot can be learned if the cipher leaks the length. This is called traffic analysis and random padding length somewhat helps against it.
a
AA
Thanks :)
PK
Padding is used to fill up plaintext to the blocklength of the cipher. This is not needed for counter mode, since it has no blocks and can encrypt any length.
There are different styles of padding, some are optimized to recognize changes or the actual length of the data. In case of the SSH sheme where a extra field specified the length no special pattern is needed, so random content provides the least information for attackers.
In SSH you can add padding longer than to the end of the block (I.e. To the next block or even more). This helps to make it harder for attackers to guess the actual plaintext length.
Especially for command/response sessions a lot can be learned if the cipher leaks the length. This is called traffic analysis and random padding length somewhat helps against it.
There are different styles of padding, some are optimized to recognize changes or the actual length of the data. In case of the SSH sheme where a extra field specified the length no special pattern is needed, so random content provides the least information for attackers.
In SSH you can add padding longer than to the end of the block (I.e. To the next block or even more). This helps to make it harder for attackers to guess the actual plaintext length.
Especially for command/response sessions a lot can be learned if the cipher leaks the length. This is called traffic analysis and random padding length somewhat helps against it.
a
Padding is used to fill up plaintext to the blocklength of the cipher. This is not needed for counter mode, since it has no blocks and can encrypt any length.
There are different styles of padding, some are optimized to recognize changes or the actual length of the data. In case of the SSH sheme where a extra field specified the length no special pattern is needed, so random content provides the least information for attackers.
In SSH you can add padding longer than to the end of the block (I.e. To the next block or even more). This helps to make it harder for attackers to guess the actual plaintext length.
Especially for command/response sessions a lot can be learned if the cipher leaks the length. This is called traffic analysis and random padding length somewhat helps against it.
There are different styles of padding, some are optimized to recognize changes or the actual length of the data. In case of the SSH sheme where a extra field specified the length no special pattern is needed, so random content provides the least information for attackers.
In SSH you can add padding longer than to the end of the block (I.e. To the next block or even more). This helps to make it harder for attackers to guess the actual plaintext length.
Especially for command/response sessions a lot can be learned if the cipher leaks the length. This is called traffic analysis and random padding length somewhat helps against it.
I thought that padding is needed for any block cipher
a
You can not decrypt not-full block, even in CRC mode, i think
J
what kind of problem, man?
see,in chacha20poly1305 packet length of this is 28 bytes with padding.if we use different padding,whole packet length will be changed,then packet will be ignored.I don't know a method to get padding length.
packr=b'\x00\x00\x00\x18'+b'\x06'+b'\x05'+b"\x00\x00\x00\x0c"+b"ssh-userauth"+b'\x00\x00\x00\x00\x00\x00'
packr=b'\x00\x00\x00\x18'+b'\x06'+b'\x05'+b"\x00\x00\x00\x0c"+b"ssh-userauth"+b'\x00\x00\x00\x00\x00\x00'
PK
see,in chacha20poly1305 packet length of this is 28 bytes with padding.if we use different padding,whole packet length will be changed,then packet will be ignored.I don't know a method to get padding length.
packr=b'\x00\x00\x00\x18'+b'\x06'+b'\x05'+b"\x00\x00\x00\x0c"+b"ssh-userauth"+b'\x00\x00\x00\x00\x00\x00'
packr=b'\x00\x00\x00\x18'+b'\x06'+b'\x05'+b"\x00\x00\x00\x0c"+b"ssh-userauth"+b'\x00\x00\x00\x00\x00\x00'
you are making your own ssh agent and you want to implement random padding with chacha20poly?
PK
packr=b'\x00\x00\x00\x18'+b'\x06'+b'\x05'+b"\x00\x00\x00\x0c"+b"ssh-userauth"+b'\x00\x00\x00\x00\x00\x00'
from what I've send about binary format of the packet, that's a padding length
from what I've send about binary format of the packet, that's a padding length