МК
Size: a a a
2021 January 18
а у линукса нет проблем с шифрованием?
УМВР
МК
там tpm все дела?
получше чем у подоконников
Д
импакт то нулевой
Its triggerable as a low privileged user- no special credentials or write permissions are needed.
The vulnerability can be remotely triggered if having any kind of service allowing file opens of specific names to happen.
Its embeddable in HTML, sharred folders etc.
The vulnerability can be remotely triggered if having any kind of service allowing file opens of specific names to happen.
Its embeddable in HTML, sharred folders etc.
SG
я так подозреваю tpm у мозолеежек это пиздец
МК
у которых только в теории блять всё работает
Д
ну крч сам можешь ознакомиться
Д
Д
имхо крит пиздец
SG
Its triggerable as a low privileged user- no special credentials or write permissions are needed.
The vulnerability can be remotely triggered if having any kind of service allowing file opens of specific names to happen.
Its embeddable in HTML, sharred folders etc.
The vulnerability can be remotely triggered if having any kind of service allowing file opens of specific names to happen.
Its embeddable in HTML, sharred folders etc.
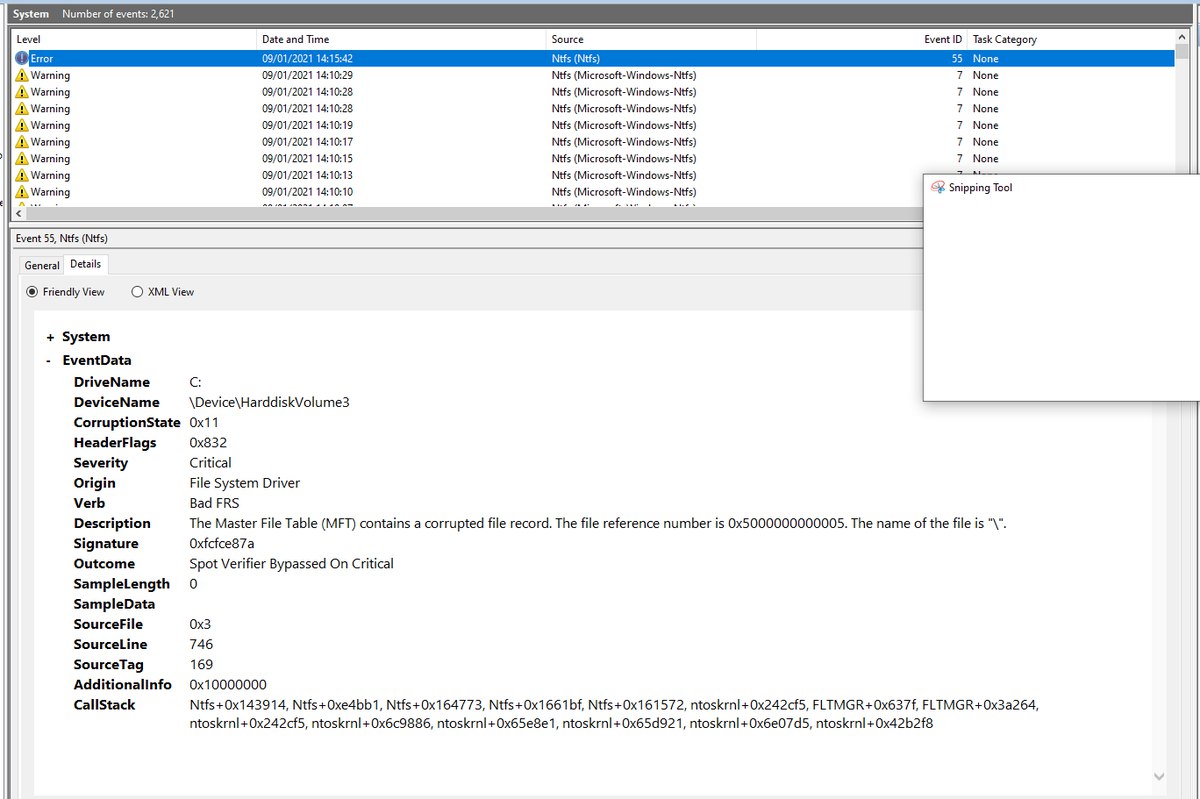
ну так импакт то какой?
SG
права поднимет?
SG
фс оно не ломает
p
а у линукса нет проблем с шифрованием?
Нет. Сколько раз выключал ноуты по power принудительно - всегда получалось загрузиться. А тут наебнулось в самый неподходящий момент.
SG
Нет. Сколько раз выключал ноуты по power принудительно - всегда получалось загрузиться. А тут наебнулось в самый неподходящий момент.
тебе повезло
SG
твоей жене нет
SG
я так же с виндой и битолокером ебал ноуты как хотел
SG
даже акк вытаскивал и нет проблем
SG
может ты просто денег пожалел на нормальный ноут?
SG
и на алишечке купил со сборкой от васяна?
p
там tpm все дела?
Нет, без tpm. Я немного помедитировал над ноутом и забил. Отдали корп. админам