v
Size: a a a
2020 June 29
Vladimir Karantaev
Что скажете?
а ожидаемых объемов к 2020 году он уже достиг?
VK
vadim.s.
а ожидаемых объемов к 2020 году он уже достиг?
Смотря у кого какие прогнозы были 😉👌
MS
Vladimir Karantaev
Что скажете?
Маловато
v
Vladimir Karantaev
Смотря у кого какие прогнозы были 😉👌
Вот-вот, а какой сейчас объем в РФ хоть кто-то знает?
VK
vadim.s.
Вот-вот, а какой сейчас объем в РФ хоть кто-то знает?
Отличный вопрос...
RK
ID:0
Новый эпизод в плэйлисте подкастов @BEERISAC: CPS/ICS Security Podcast Playlist: "Beer ISAC, Beer ISAC podcast and other initiatives Kaspersky Support" из подкаста The Industrial Security Podcast
Рассказал в нем так же о развитии сообщества RUSCADASEC
http://bit.ly/beerisac
Рассказал в нем так же о развитии сообщества RUSCADASEC
http://bit.ly/beerisac
что-то ведущие какие-то очень скептические
AS
что-то ведущие какие-то очень скептические
Почему?
RK
делаем интервью с Касперским (которые помогли IOT консорциуму с практическим документом и который распространяется бесплатно) потом фигак "мы американцы ISA тут все выпустили а они европейцы с IEC просто его перепродают, вступайте в армию ISA"
NK
https://www.us-cert.gov/ics/advisories/icsa-20-177-02
IMPROPER RESTRICTION OF XML EXTERNAL ENTITY REFERENCE CWE-611
A remote, unauthenticated attacker could use an XML External Entity (XXE) attack to exploit weakly configured XML files to access local or remote content. A successful exploit could potentially cause a denial-of-service condition and allow the attacker to arbitrarily read any local file via system-level services.
IMPROPER RESTRICTION OF XML EXTERNAL ENTITY REFERENCE CWE-611
A remote, unauthenticated attacker could use an XML External Entity (XXE) attack to exploit weakly configured XML files to access local or remote content. A successful exploit could potentially cause a denial-of-service condition and allow the attacker to arbitrarily read any local file via system-level services.
NK
Rockwell Automation received a report from Ilya Karpov and Evgeny Druzhinin who are part of the independent research team, ScadaX Security. They reported two vulnerabilities in FactoryTalk® View Site Edition (SE) software, which if successfully exploited, may result in the disclosure of Windows® Logon credentials (via the DeskLock software) or FactoryTalk View SE user credentials.
Affected Products
CVE-2020-14480: FactoryTalk View SE versions 9.0 and earlier.
CVE-2020-14481: FactoryTalk View SE version 10.0.
Vulnerability Details:
CVE-2020-14480: Cleartext Storage of Sensitive Information in Memory
A local, authenticated attacker may have access to certain credentials, including Windows Logon credentials, as a result of usernames/passwords being stored in plaintext in Random Access Memory (RAM).
CVSS v3.1 Base Score: 8.8/HIGH
CVE-2020-14481: Use of a Weak Algorithm for Password Protection
The DeskLock tool provided with FactoryTalk View SE uses a weak encryption algorithm that may allow a local, authenticated attacker to decipher user credentials, including the Windows user or Windows DeskLock passwords. If the compromised user has an administrative account, an attacker could gain full access to the user’s operating system and certain components of FactoryTalk View SE.
CVSS v3.1 Base Score: 8.8/HIGH
https://rockwellautomation.custhelp.com/app/answers/answer_view/a_id/1127024/redirect
Affected Products
CVE-2020-14480: FactoryTalk View SE versions 9.0 and earlier.
CVE-2020-14481: FactoryTalk View SE version 10.0.
Vulnerability Details:
CVE-2020-14480: Cleartext Storage of Sensitive Information in Memory
A local, authenticated attacker may have access to certain credentials, including Windows Logon credentials, as a result of usernames/passwords being stored in plaintext in Random Access Memory (RAM).
CVSS v3.1 Base Score: 8.8/HIGH
CVE-2020-14481: Use of a Weak Algorithm for Password Protection
The DeskLock tool provided with FactoryTalk View SE uses a weak encryption algorithm that may allow a local, authenticated attacker to decipher user credentials, including the Windows user or Windows DeskLock passwords. If the compromised user has an administrative account, an attacker could gain full access to the user’s operating system and certain components of FactoryTalk View SE.
CVSS v3.1 Base Score: 8.8/HIGH
https://rockwellautomation.custhelp.com/app/answers/answer_view/a_id/1127024/redirect
AI
Индепендент рисёрчерз Карпофф энд Дружинин ? ))
MY
Индепендент рисёрчерз Карпофф энд Дружинин ? ))
мы и индепендед и не индепендед бываем), выходные никто не отменял)
AI
Ребят, молодцы!
IM
Для новичков стакснет подвезли. Вебинар от карбонблека 21 июля: Stuxnet and Beyond: The Age of Digital Warfare and the Future of Our Cities https://www.carbonblack.com/resource/stuxnet-and-beyond-the-age-of-digital-warfare-and-the-future-of-our-cities/
C
Для новичков стакснет подвезли. Вебинар от карбонблека 21 июля: Stuxnet and Beyond: The Age of Digital Warfare and the Future of Our Cities https://www.carbonblack.com/resource/stuxnet-and-beyond-the-age-of-digital-warfare-and-the-future-of-our-cities/
_________________
There have been
⛑️ 0 days ⛑️
since Stuxnet
was mentioned
There have been
⛑️ 0 days ⛑️
since Stuxnet
was mentioned
AS
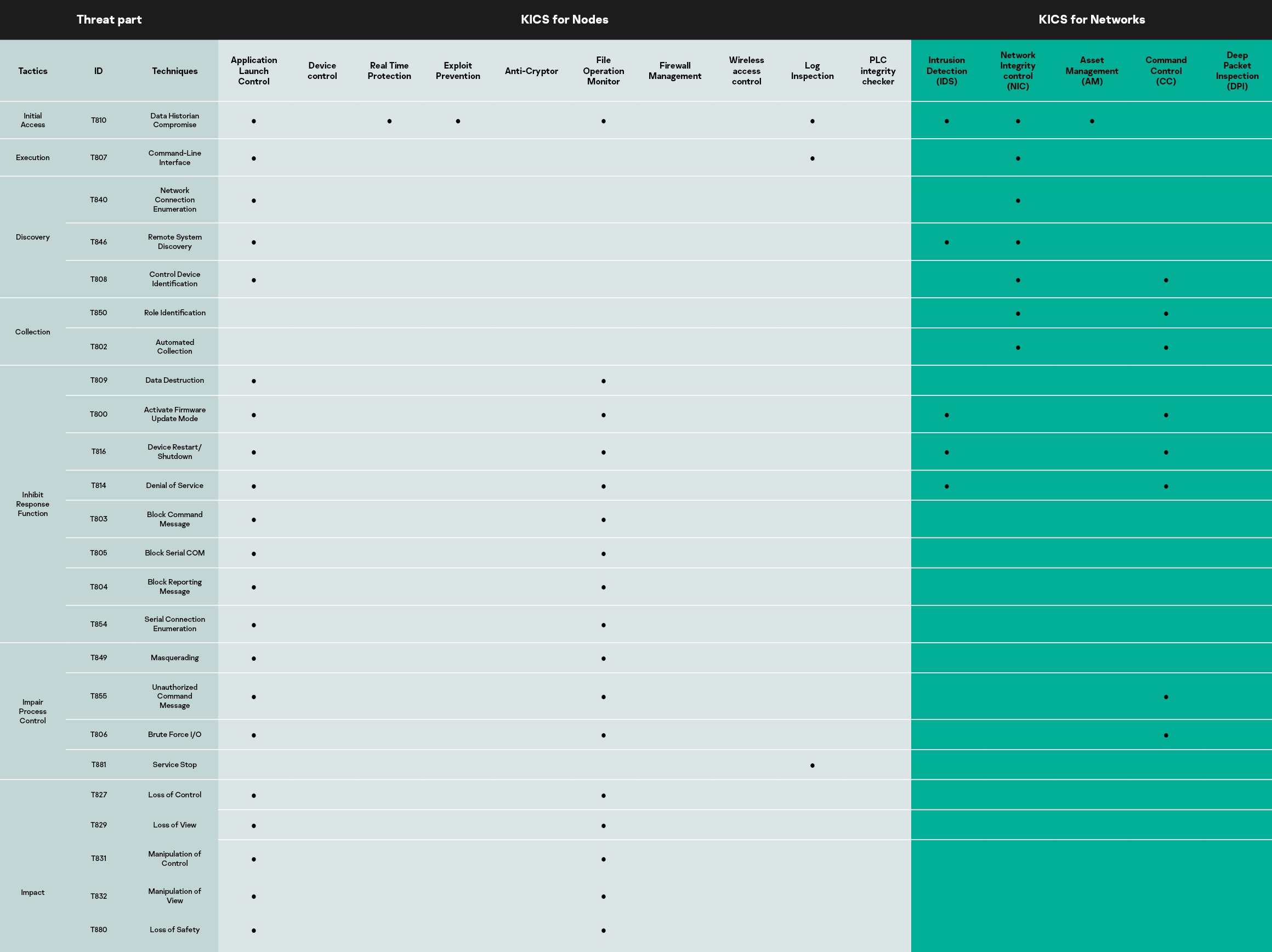
Обновили с коллегами статью с подробной демонстрацией как Kaspersky Industrial Cybersecurity, KICS for Nodes и KICS for Networks могли бы вместе обнаружить техники по матрице MITRE ATT&CK ICS для Industroyer/CRASHOVERRIDE (Атака на украинскую подстанцию «Северная» в 2016 году)
https://www.kaspersky.com/enterprise-security/mitre/industroyer
https://www.kaspersky.com/enterprise-security/mitre/industroyer
2020 June 30
S
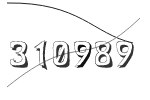
Это антиспам проверка!
@shuzhynodaexugy206, пожалуйста, отправьте цифры с картинки в этот чат в течение указанного времени (200 сек), иначе вы будете удалены из группы (с возможностью повторного подключения через 2 минуты). Спасибо!
***
It is an antispam test!
@shuzhynodaexugy206, please, send the characters displayed within the time amount specified (200 sec) to this group, otherwise you will be kicked (with a new attempt to join in 2 minutes). Thank you!
@shuzhynodaexugy206, пожалуйста, отправьте цифры с картинки в этот чат в течение указанного времени (200 сек), иначе вы будете удалены из группы (с возможностью повторного подключения через 2 минуты). Спасибо!
***
It is an antispam test!
@shuzhynodaexugy206, please, send the characters displayed within the time amount specified (200 sec) to this group, otherwise you will be kicked (with a new attempt to join in 2 minutes). Thank you!
SP
SP
КИИ на очереди?






