Size: a a a
2017 May 12

Евгений Касперский хочет оправдаться перед сенатом США http://safe.cnews.ru/news/top/2017-05-12_evgenij_kasperskij_gotov_svidetelstvovat_pered <p>Глава «Лаборатории Касперского» готов дать показания перед лицом Сената США. Такое желание он высказал после того, как руководители разведслужб США заявили Сенату, что не доверяют продуктам его компании и избегают использовать их в своих сетях. Причина — возможные связи «Лаборатории» с российским правительством, в пользу которого она якобы занимается кибершпионажем.<br></p>

В ноутбуках HP обнаружили аудиодрайвер, выполнявший функции кейлоггера https://xakep.ru/2017/05/12/hp-laptops-spying-on-you/ <img alt src=


«Доктор Веб» обнаружила новый бэкдор для Mac http://safe.cnews.ru/news/line/2017-05-12_doktor_veb_obnaruzhila_novyj_bekdor_dlya_mac Троянец-бэкдор добавлен в вирусные базы Dr.Web под именем Mac.BackDoor.Systemd.1

Исследователи научились создавать фальшивые цифровые отпечатки для разблокировки смартфонов https://xakep.ru/2017/05/12/masterprints/ <img alt src=

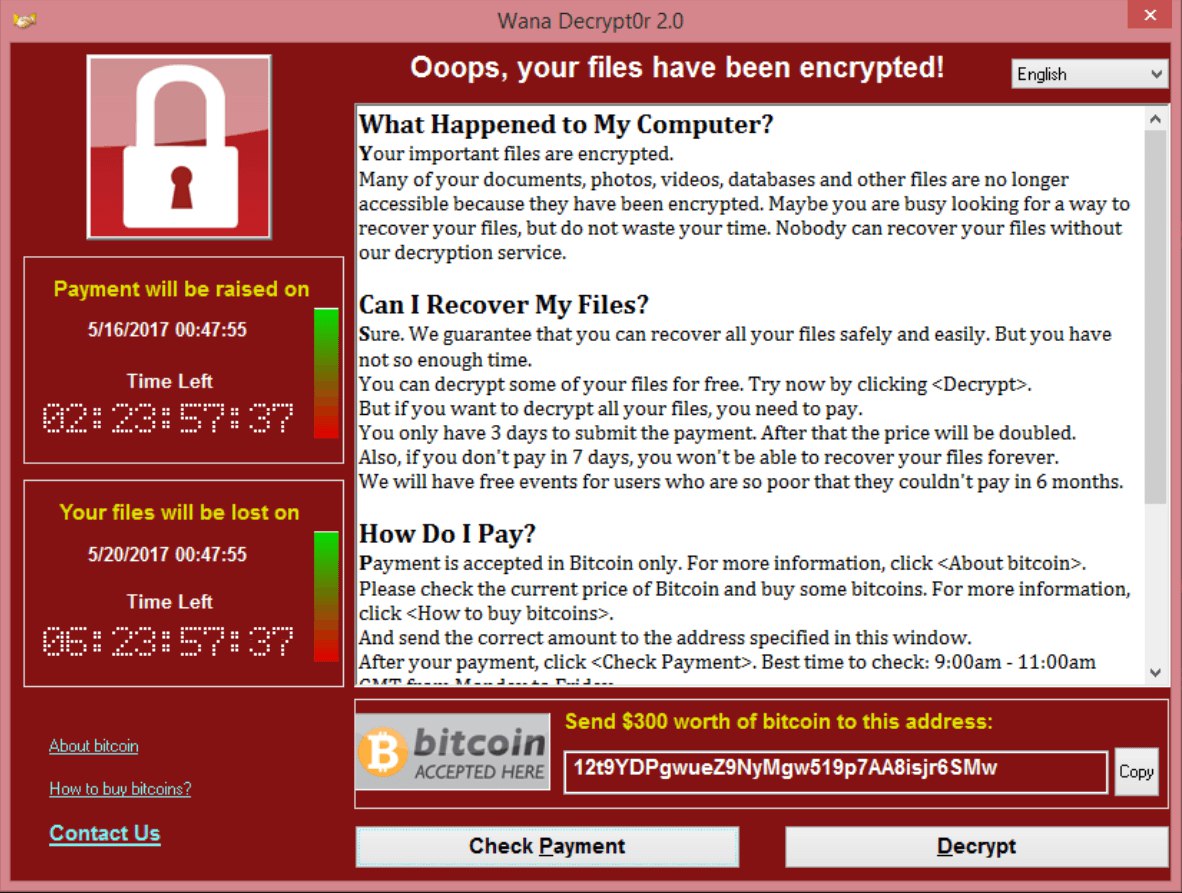
Компьютеры МВД по всей России поражены трояном-шифровальщиком. Видео http://safe.cnews.ru/news/top/2017-05-12_kompyutery_mvd_po_vsej_rossii_porazheny_troyanomshifrovalshchikom <p>Рабочие компьютеры полицейских в рядке регионов России
оказались заражены вирусом-вымогателем. Троян шифрует пользовательские файлы, а
за обратную дешифровку требует выкуп.</p>
оказались заражены вирусом-вымогателем. Троян шифрует пользовательские файлы, а
за обратную дешифровку требует выкуп.</p>

По всему миру активизировался Троян шифровальщик WanaCryptor. Он использует уязвимости в SMB для распространения. Говорят накрыло МВД в РФ и задело много других компаний. Если нужна помощь - пишите.
Дальше идут рекомендации от нашей Incident Response Team: Check Point offers the following protections for WanaCryptor
1. Anti-Bot/Anti Virus on endpoint with Sand Blast Agent and Anti-Bot/Anti Virus on Security Gateway
2. Anti-Ransomware on endpoint with Sand Blast Agent
3. Windows machines should be patched for vulnerabilities discussed in Microsoft Security Bulletin MS17-010 - Critical Security Update for Microsoft Windows SMB Server (4013389) https://technet.microsoft.com/en-us/library/security/ms17-010.aspx .
4. Depending on the network architecture, the following IPS protections may be deployed to mitigate the worming properties of this attack.
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0143)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0177.html
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0144)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0198.html
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0145)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0200.html
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0146)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0203.html
Microsoft Windows SMB Information Disclosure (MS17-010: CVE-2017-0147)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0205.html
The Check Point Incident Response Team is monitoring the situation closely and is available to assist customers.
Дальше идут рекомендации от нашей Incident Response Team: Check Point offers the following protections for WanaCryptor
1. Anti-Bot/Anti Virus on endpoint with Sand Blast Agent and Anti-Bot/Anti Virus on Security Gateway
2. Anti-Ransomware on endpoint with Sand Blast Agent
3. Windows machines should be patched for vulnerabilities discussed in Microsoft Security Bulletin MS17-010 - Critical Security Update for Microsoft Windows SMB Server (4013389) https://technet.microsoft.com/en-us/library/security/ms17-010.aspx .
4. Depending on the network architecture, the following IPS protections may be deployed to mitigate the worming properties of this attack.
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0143)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0177.html
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0144)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0198.html
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0145)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0200.html
Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0146)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0203.html
Microsoft Windows SMB Information Disclosure (MS17-010: CVE-2017-0147)
https://www.checkpoint.com/defense/advisories/public/2017/cpai-2017-0205.html
The Check Point Incident Response Team is monitoring the situation closely and is available to assist customers.

Шифровальщик Wana Decrypt0r одновременно атаковал десятки компаний и организаций по всему миру https://xakep.ru/2017/05/12/wcry-ransomware-apocalypse/ <img alt src=

Вирус-вымогатель поразил компьютеры по всему миру и добрался до России https://www.anti-malware.ru/news/2017-05-12/22934 <img alt=

Хакеры взламывали юридические фирмы и использовали инсайдерские данные для скупки акций https://xakep.ru/2017/05/12/insider-trading-scam/ <img alt src=
2017 May 13

PHDays HackQuest 2017: RanSomWare — небольшой криптор на GO https://habrahabr.ru/post/328114/ Всем доброго времени суток, только что подошел к концу двухнедельный <a href=

74 страны захлестнула волна атак с использованием вымогателя WannaCry http://www.securitylab.ru/news/486124.php <img src=

Международную кибератаку остановил один программист https://www.anti-malware.ru/news/2017-05-13/22935 <img alt=

Тенденции IT-рынка: всё умнеет, даже киберпреступники - IT-Weekly http://news.google.com/news/url?sa=t&fd=R&ct2=us&usg=AFQjCNHbYksnluDha6i4XxmwPybcZ-N-qw&clid=c3a7d30bb8a4878e06b80cf16b898331&ei=-CEXWaiNE8WrhQGJia-QDA&url=http://www.it-weekly.ru/it-news/security/118646.html <table cellpadding=

Британец временно приостановил вирус-вымогатель http://www.securitylab.ru/news/486125.php <div><div class=

Исследователь остановил распространение Wana Decrypt0r, а Microsoft выпустила патч для XP https://xakep.ru/2017/05/13/wana-decrypt0r/ <img alt src=

Парень случайно остановил глобальное распространение криптовымогателя WannaCrypt https://geektimes.ru/post/289143/ В эти дни все только и говорят о <a href=
2017 May 14

Microsoft обновила неподдерживаемые версии Windows для защиты от атак WannaCry http://www.securitylab.ru/news/486126.php <img src=

Матвиенко: информационная безопасность детей должна обсуждаться на международном уровне - Рамблер Новости http://news.google.com/news/url?sa=t&fd=R&ct2=us&usg=AFQjCNEpLi0Oe85i3usis6JpHxL_Kuhqfg&clid=c3a7d30bb8a4878e06b80cf16b898331&cid=52780049805258&ei=koMYWZCXPMqUhQG1mrv4Dg&url=https://news.rambler.ru/kids/36704769-matvienko-informatsionnaya-bezopasnost-detey-dolzhna-obsuzhdatsya-na-mezhdunarodnom-urovne/ <table cellpadding=